An elderly Australian man went to bed on Tuesday of last week with his slippers under his bed, but woke up Wednesday morning to find only one of the slippers waiting for him.
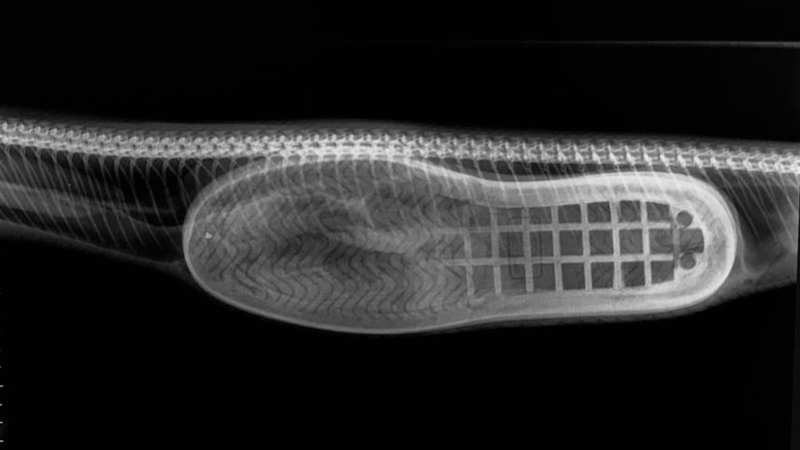
When the man went looking for his slipper days later, he found it. Or at least he found a python with a slipper-sized bulge inside it, according to Australia outlet The Courier-Mail.
The man called snake catchers Sally and Norman Hill to apprehend the python. “You could feel the rubber in its stomach, you could feel the sole of the slipper through the skin,” Sally Hill told Australia’s ABC News. “My opinion is a rat or possum crawled all over the slipper, or peed on it, or maybe there was a rat or mice in it and the snake saw it.”
Australia is a magical place.
The snake then went to veterinarian Josh Llinas so the serpent and slipper could be saved.
Llinas is used to removing strange things from snakes. “I had a pillow case removed from a black-headed python, and just a few months ago, I had a tennis ball removed from a snake,” Llinas told The Courier-Mail. “This was probably one of the more unusual things I’ve removed. I’ve heard of others swallowing thongs, stuffed toys. You name it, they will eat it.”
Llinas took an X-ray, but could tell immediately the problem was that the snake had swallowed a shoe. “Sometimes you can remove the foreign bodies by helping them after they’ve been relaxed … by helping them move it up the digestive tract and out of the mouth.” Llinas told The Courier-Mail. “This was just way too big and it wasn’t going to come out.”
Here’s a Facebook video of the [Warning: Graphic] surgery.
Llinas performed a coeliotomy and gastrotomy surgery to remove the slipper, then closed up the snake’s stomach. The snake will spend the next several weeks in recovery before it goes on to hunt for other strange things to eat.



 (@APompliano)
(@APompliano) 



 RSS Feed
RSS Feed
